With an increasing interest in cyber as a business function, it is vital that non-technical leaders are tuned into the cyber posture of their organization. Non-technical visualizations of data are in demand for these leaders to understand the state of cyber Cybersecurity dashboards aggregate and consolidate data into functional, presentable, easy-to-understand visualizations and tables that illustrate cybersecurity posture in real-time.
The CyberStrong Executive Dashboard enables Chief Information Security Officers (CISO) to gain real-time insight into their organization’s cybersecurity posture via integrated cyber risk management. A solution that integrates and acts as a single source of truth for cybersecurity program data enables teams to complete assessments faster while also automating much of the reporting process. Data is aggregated and rolled up into a single platform without the hindrance of modules. This single-pane-of-glass saves security practitioners time and provides a true sense of the organization's cybersecurity posture with visualized information that is easy to digest.
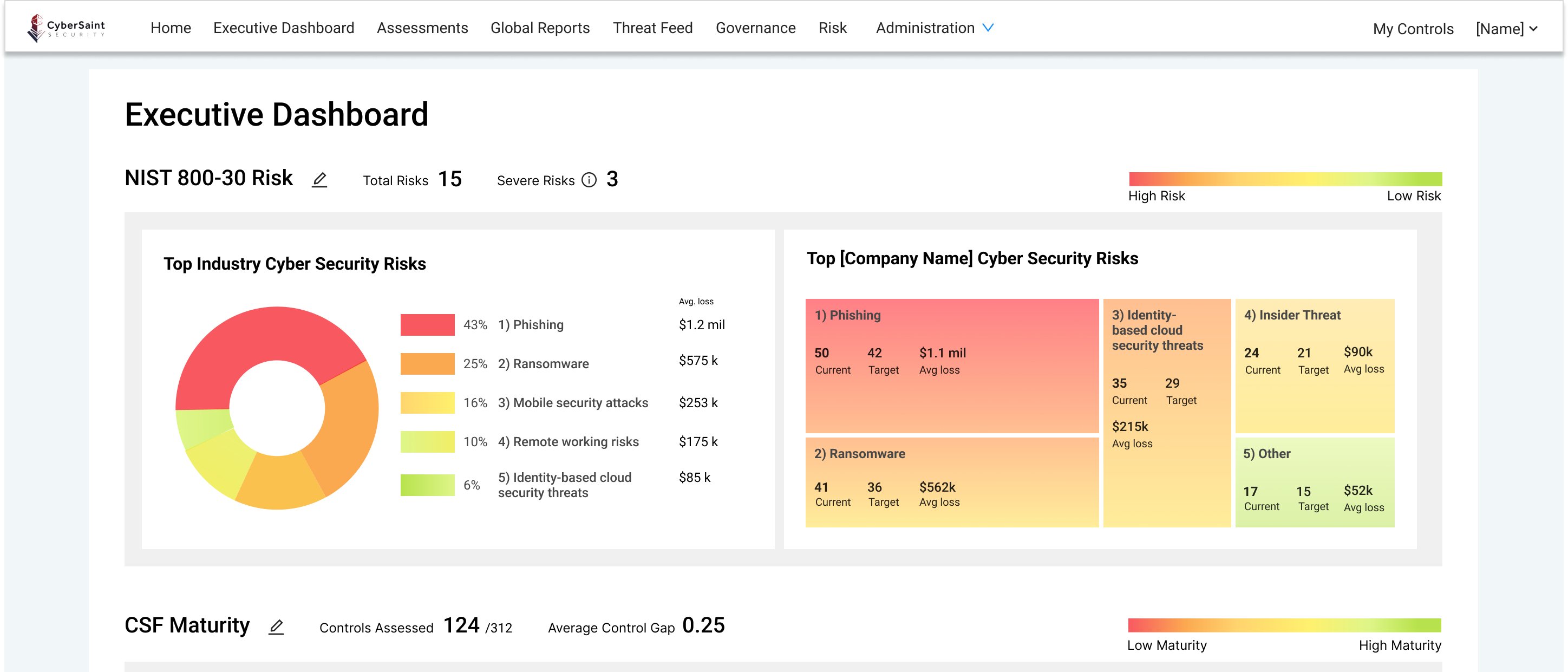
In terms of visualization, elegant user experiences use color-coding, such as the traffic light protocol, to convey information as fast as possible.
This allows users to see where the program is weakest, varying levels of risk based on assessment, and displays where leaders could invest more. Furthermore, in the case of a cyber security risk dashboard, breaking the roll-up data down into the cyber risk by the business impact and risk by threat type lends immediate, real-time visibility into the most significant risks to the organization from a high level. These can be broken down further into risk assessment reports that can guide risk mitigation activities.
The Executive Dashboard features top industry cyber security risks fueled by the Advisen data set. This dashboard utilizes Advisen cyber loss data, a data set of cyber risk actuarial data that enriches a comparison of your risk posture to industry and company-size peers. The top industry cyber security risks item varies by selected industry, revenue range, and company size range. This tool highlights your organization's top cyber security risks using Continuous Control Automation (CCA) and manual score data. Finally, the Executive Dashboard highlights framework maturity, using the CSF or another framework, such as FedRAMP, GDPR, HIPAA, and other gold-standard frameworks. This section highlights your program’s historical maturity compared to these frameworks over time.
In short, the Executive Dashboard is excellent for CISOs and executive leaders to get a sense of their organization’s cyber posture instantly using a traffic light protocol, seeing granular insight for interested non-technical stakeholders that want real-time updates, and quelling concerns about the state of security and seeing program activity from a high level to track progress to remediation and assessment.
Contact us to learn more about CyberStrong’s dashboarding and reporting capabilities.





.png)
.png)
.png)
%201.png)
.png)




