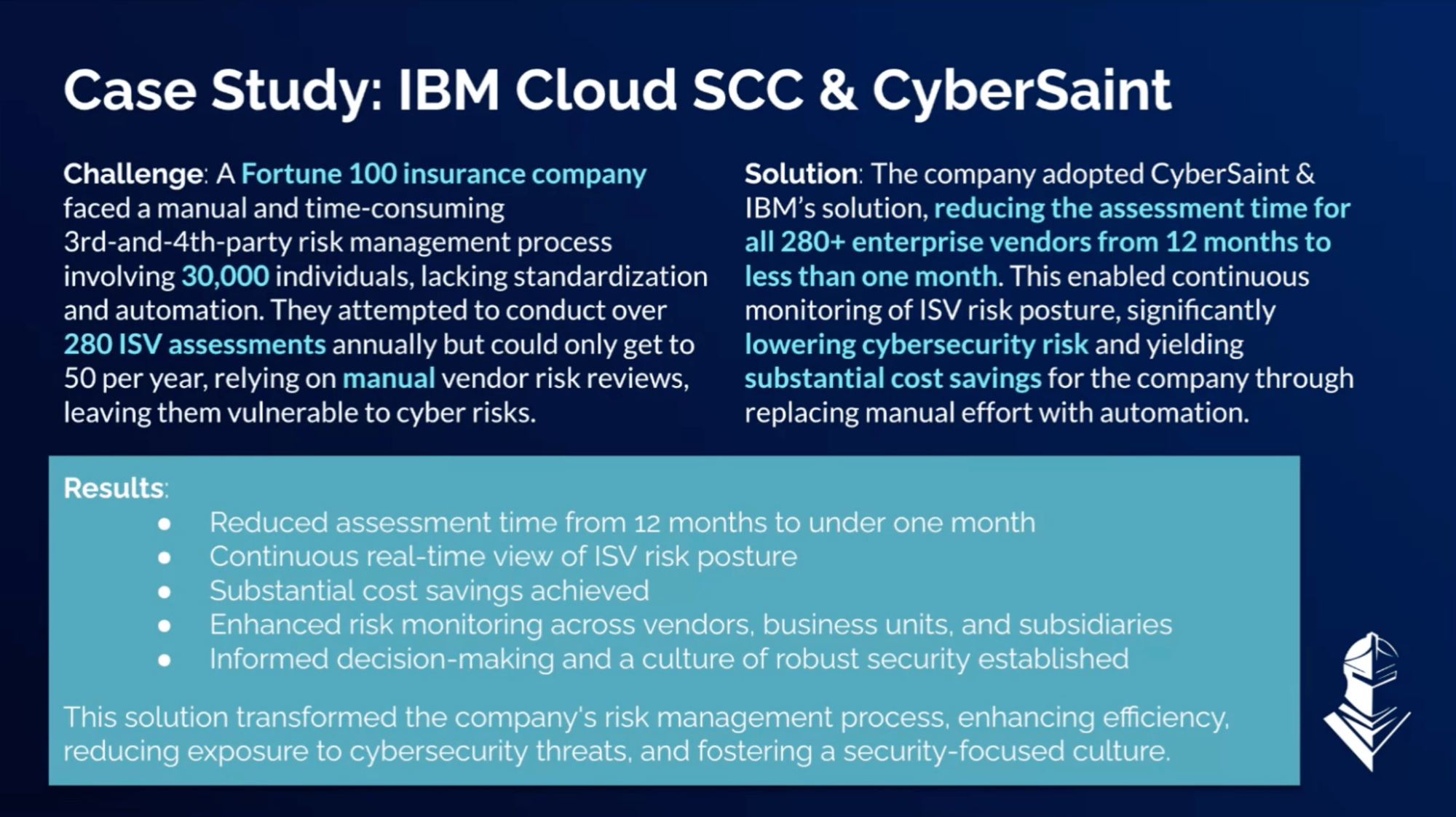
Enterprises are aggressively scaling vendor ecosystems, but the frequency and sophistication of attacks on 3rd-and-4th parties are also on the rise.
Enterprises globally utilize independent software vendors (ISVs) to accelerate their operations.
However, organizations often face difficulties in obtaining sufficient visibility into their vendor ecosystem and critical security tools, monitoring their risk posture, and verifying that they meet their critical compliance demands.
In response to these challenges, CyberSaint and IBM Cloud have collaborated to give organizations the ability to gain visibility and automate control compliance across third-and-fourth-party ecosystems.
Automate Vendor Ecosystem Control Assessments
CyberStrong pulls in data from IBM Cloud Security and Compliance Center to automate policy updates and deliver real-time ISV alerts. CyberStrong's continuous control automation scores controls, monitors compliance, and assesses your vendors' real-time posture against frameworks. Monitor when controls fall out of compliance and why while rolling up to actionable insights.
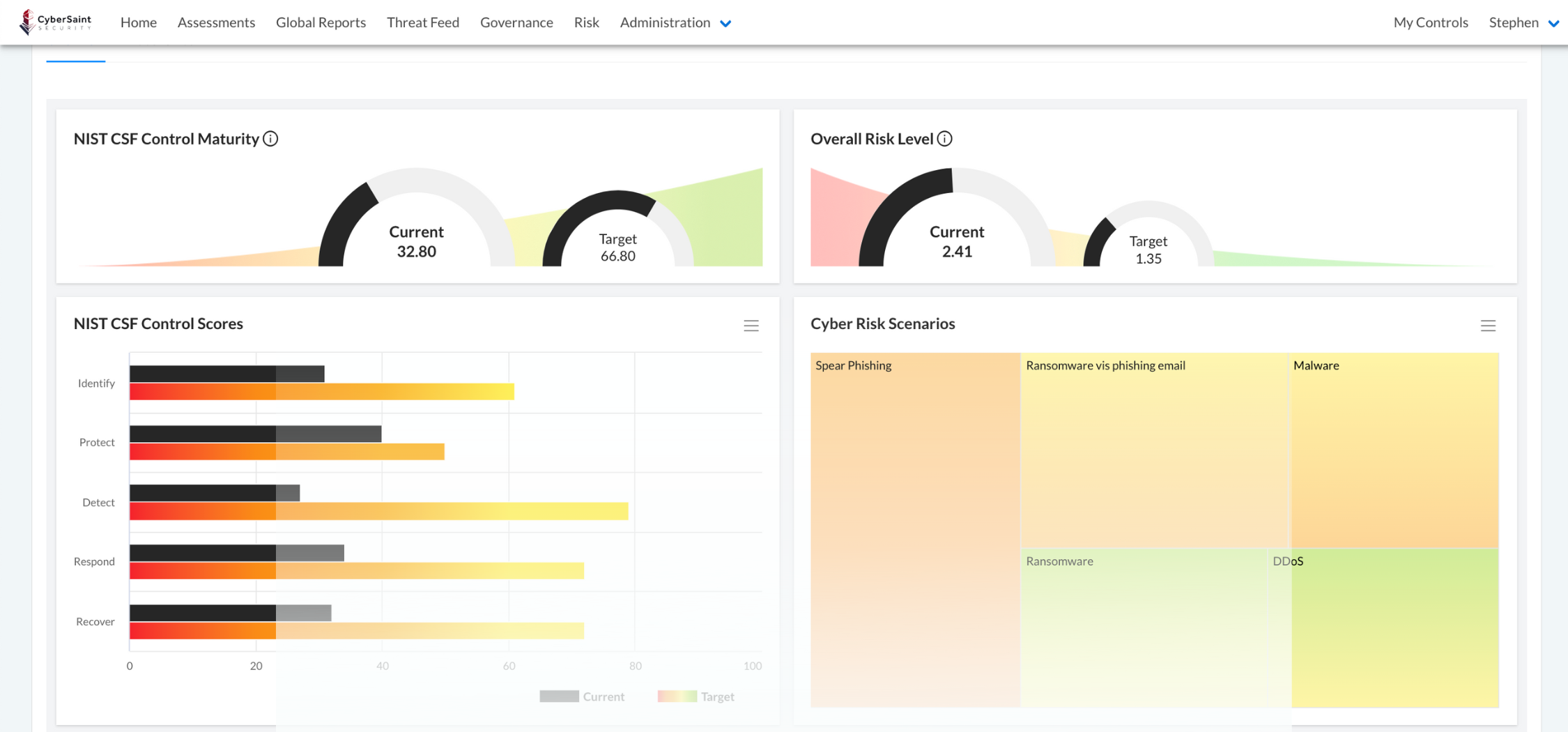
Quantify Cyber Risk and Utilize Advanced Analytics
CyberStrong automates risk analysis by pulling security control groupings onto identified risks. Customers can choose their risk model (qualitative, quantitative, threat-based, etc.) and apply IBM SCC feeds to analyze gaps and residual risk on the Financial Services profile and more frameworks. Utilize methods like the FAIR model to communicate risk in dollars, run scenario analysis, and track against goals.
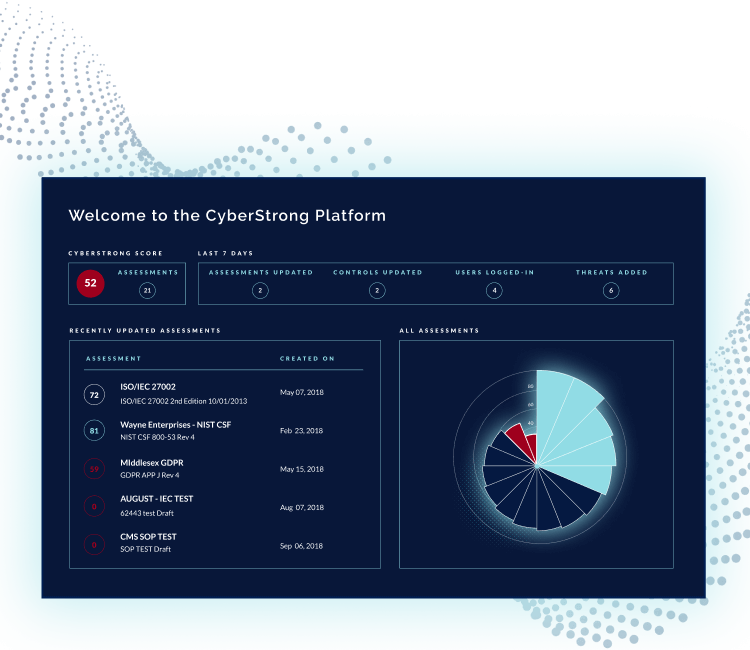
Achieve Clear Visibility and Seamless Communication
Gain actionable cyber posture assessments and a continuous view of vendor ecosystem risk, resulting in lowered business risk and significant cost savings. Monitor and evaluate risks across vendors, business units, and subsidiaries in real-time, with intuitive reports, dashboards, and graphics.
.png?width=2000&name=Product%20Screenshots%20(2).png)
Executive Risk Dashboarding
.png?width=1500&height=700&name=Product%20Screenshots%20(3).png)
Vendor Comparisons
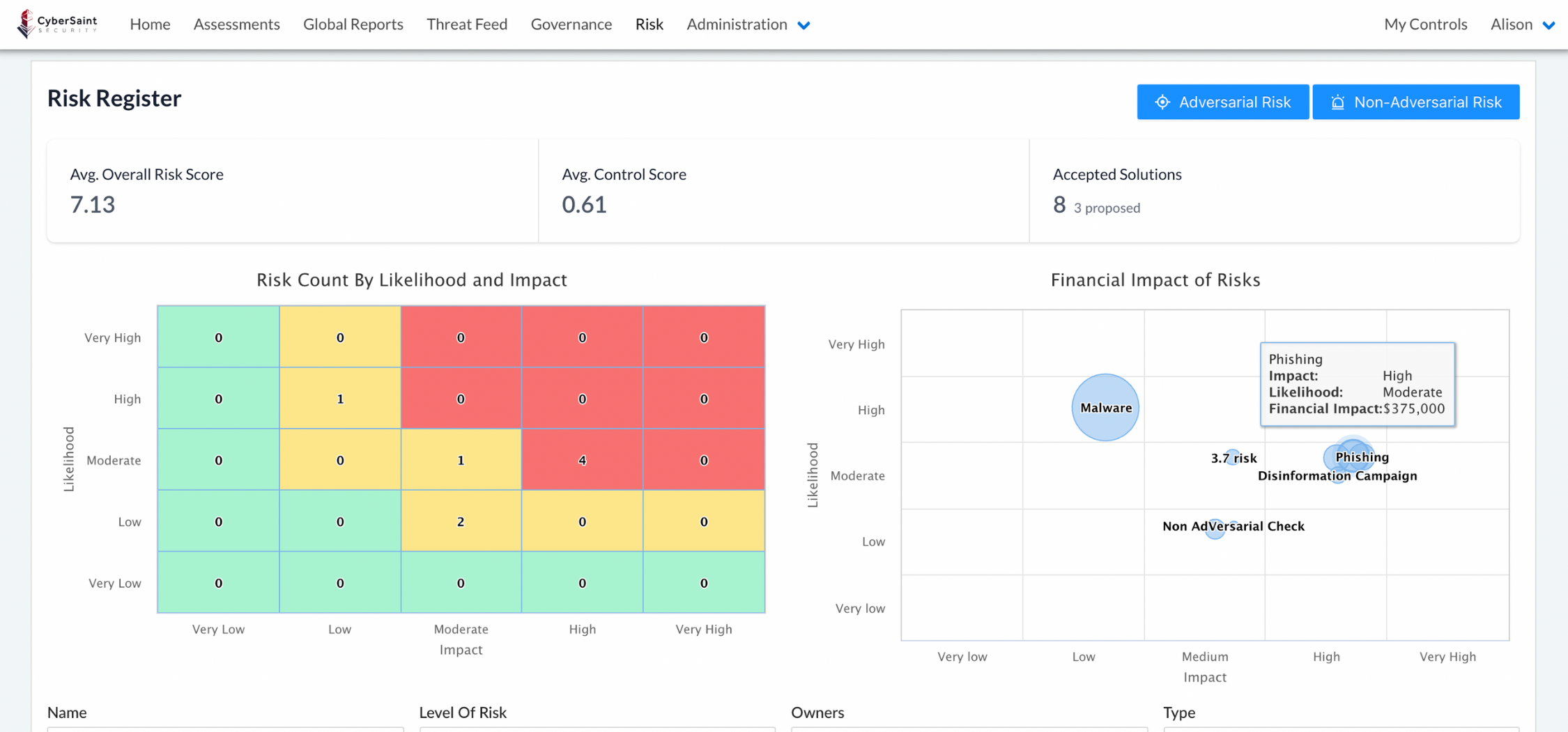
Risk Register
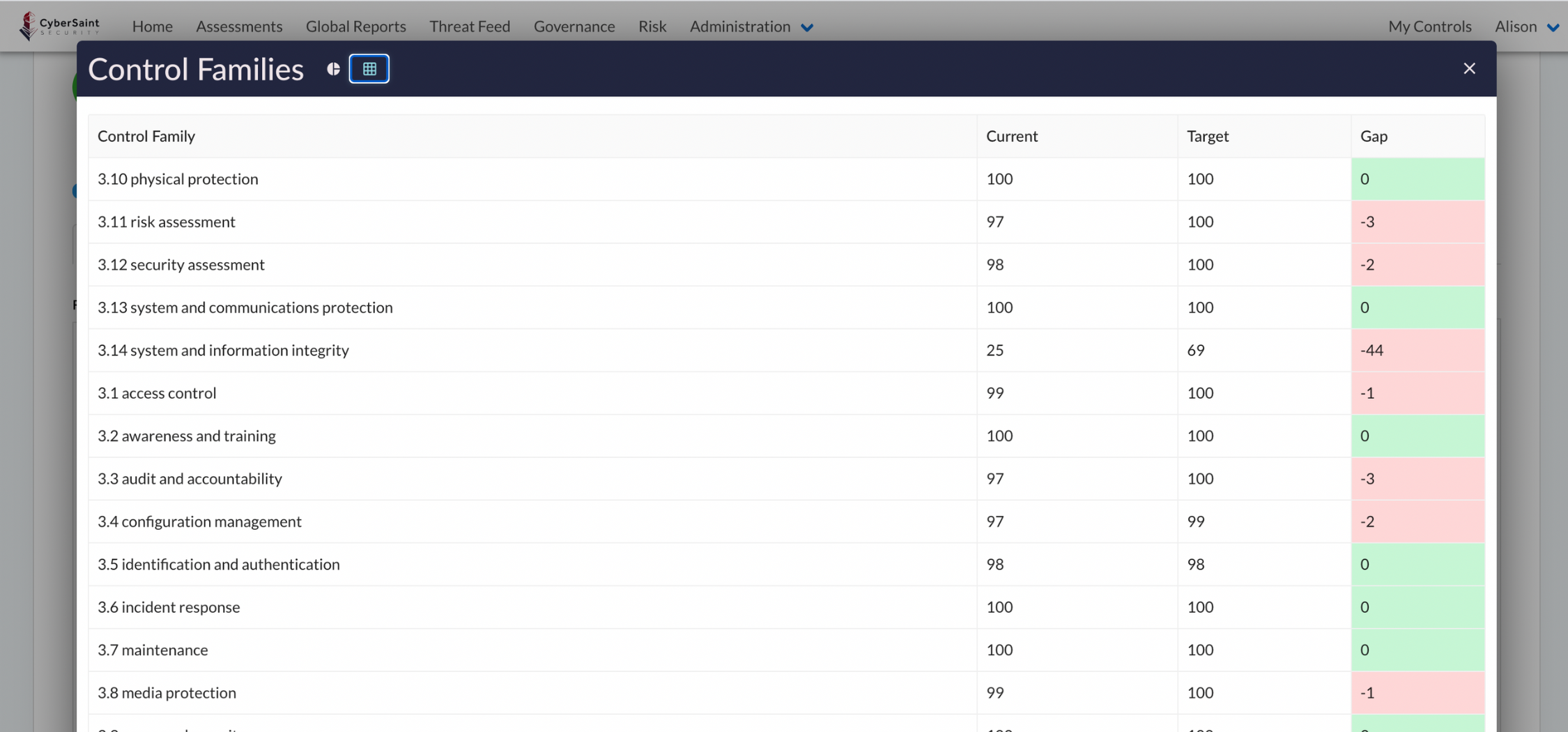
Automated Control Assessment
How Customers Experience
Solution Value
With the ability to assess enterprise vendors in significantly reduced timeframes, monitor risks across the organization, and promote a culture of robust security, enterprises are empowered to enhance their cyber resilience and navigate the complex landscape of vendor relationships with confidence.
Video Overview