Everyone knows curiosity killed the cat, but with this update, it’s killed the Contributor. As an add-on to the latest release, we’ve put Contributors’ noses back where they belong - in My Controls.
Now, some of you may be wondering, “Why such harsh restrictions? Who was the bad egg that prompted this TSA-level crackdown on Contributors?”
Well, historically, telling someone not to press the red button hasn’t actually prevented them from pressing the red button, has it? (Hopefully, you see where this is going) Instead, it makes them hyper-fixate on it. “What does the red button do? Why can’t I press it? Who can press it? Oooooh, there’s a blue button! They didn’t say anything about the blue button - can I press that one?” You get the drift… If you really don’t want someone to press a button, don’t give them access to the button.
The same solution applies to audits. For many of our customers, the integrity of their audits can only be guaranteed when Contributor visibility is limited to fields where their direct input is required. For most, the Contributor must provide evidence of compliance with an accompanying annotation - nothing more, nothing less. Exposing them to additional inputs (e.g., the risk assessment tab, completion cost) could influence their compliance statements and/or make it harder for them to discern which fields are theirs to populate - neither of which are conducive to an audit.
So, think of this lockdown as more of a precaution designed to refocus efforts than a “punishment.”
Keep reading below to see how Administrators can streamline Contributor inputs by restricting access to fields outside of the My Controls page:
To prevent Contributors from navigating away from My Controls, follow the step-by-step guidance outlined below:
- Log into the CyberStrong platform as a user with Administrator access.
- Navigate to the ‘Administration’ tab within the home navigation bar and select ‘Settings’ from the dropdown menu.
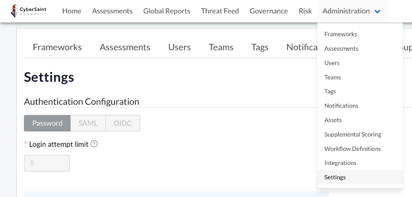
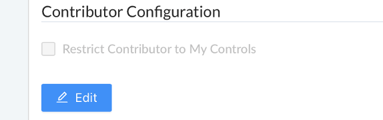
- Navigate to the ‘Contributor Configuration’ section of the ‘Settings’ page and click the blue ‘Edit’ button below the ‘Restrict Contributor to My Controls’ checkbox.
Once you click the blue ‘Edit’ button, the ‘Restrict Contributor to My Controls’ checkbox will no longer be grayed out and can be checked.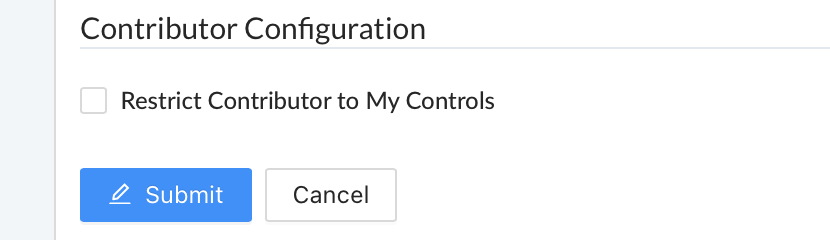
- Check the ‘Restrict Contributor to My Controls’ checkbox and click the blue ‘Submit’ button below the checkbox to confirm your entry.
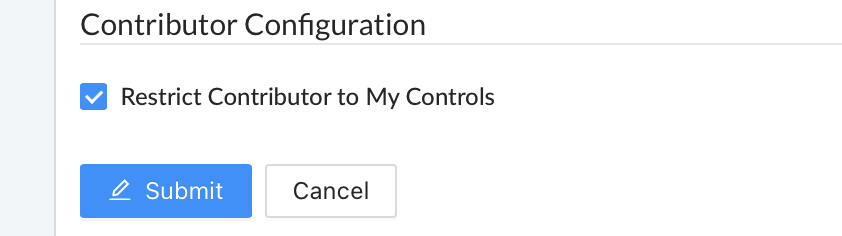
Once you click the blue ‘Submit’ button, the section will return to being grayed out.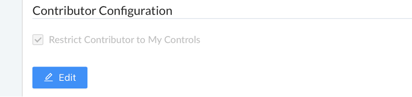
Note: By default, the ‘Restrict Contributor to My Controls’ checkbox is unchecked. Checking the box will restrict access for all Contributors within the environment, regardless of which frameworks and assessments they have been assigned controls from.
Unchecked
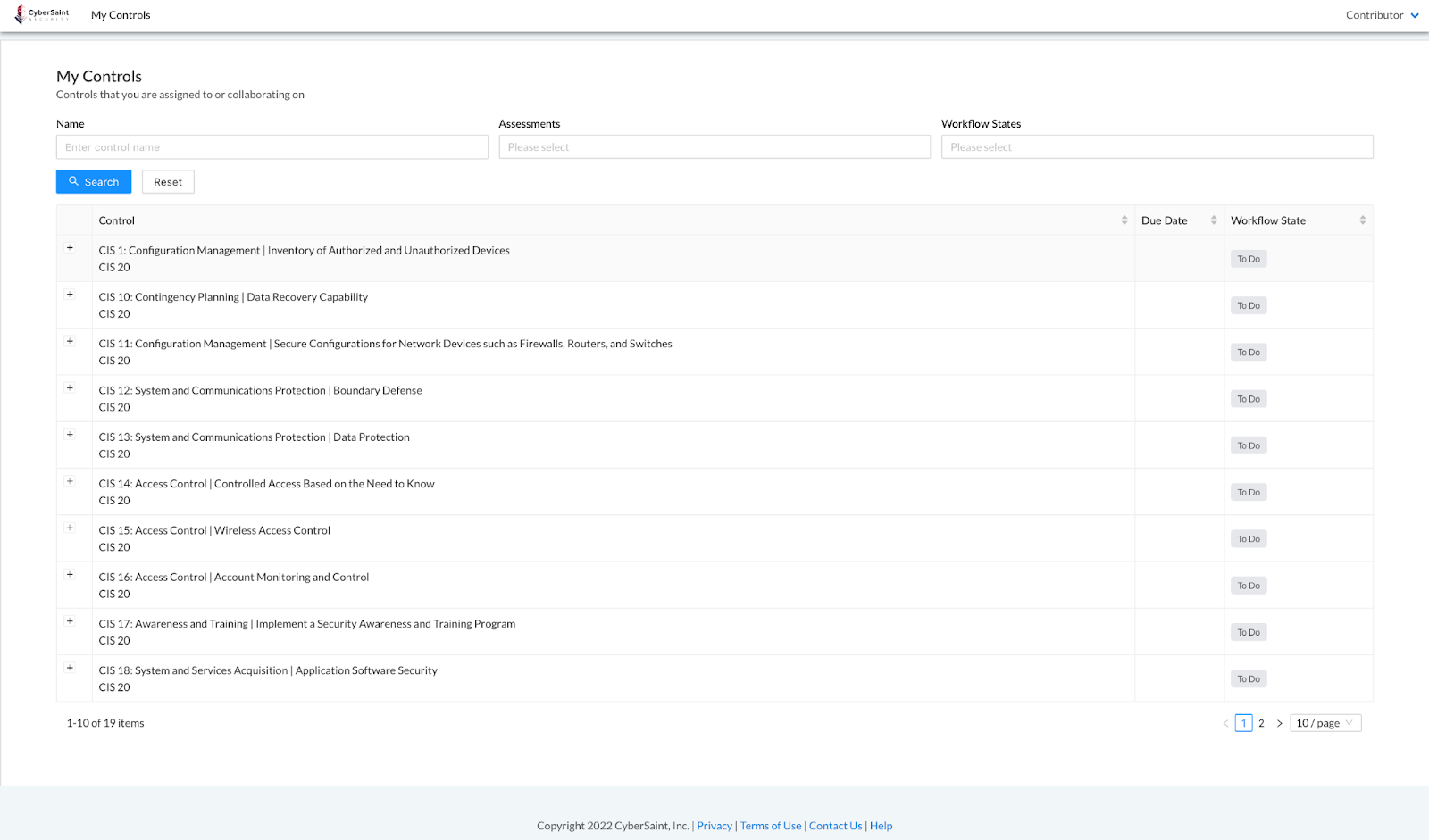
When the checkbox is NOT checked, Contributors can navigate to the control page from the My Controls tab by clicking the hyperlink title of the control.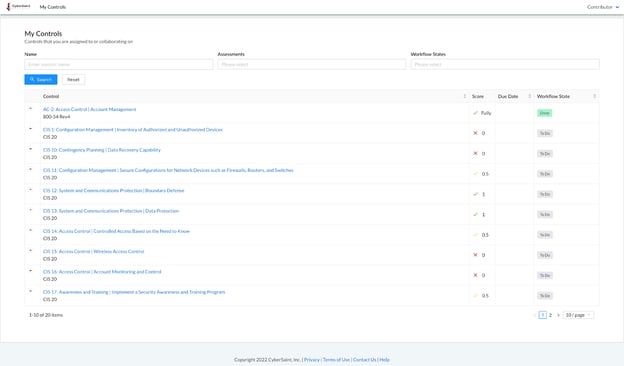
Once on the control page, they can access all fields related to that control - including the other control tabs (e.g., Risk Assessment).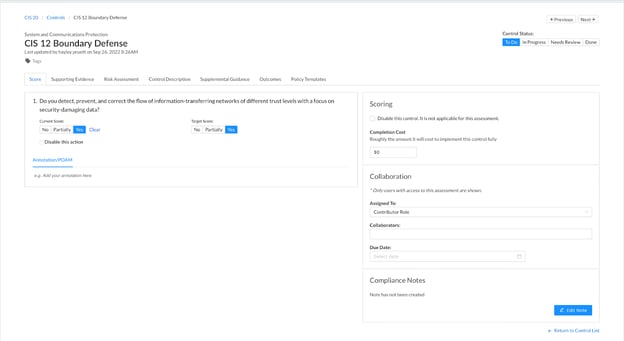
Checked
When the checkbox IS checked, the hyperlinks will be removed from the titles of controls, and Contributors cannot navigate to the control page.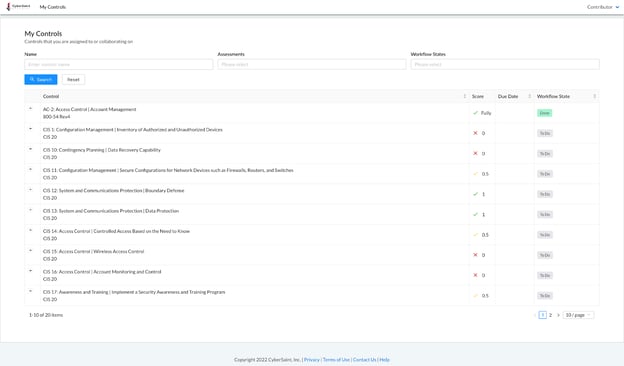
Instead, Contributors can only add inputs to controls via the My Controls page by clicking the ‘+’ icon to the left of each control.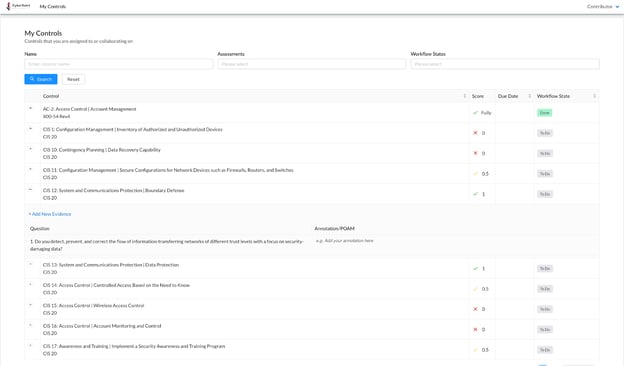
Once the details for a control have been expanded, the Contributor can add evidence by clicking the blue ‘+ Add New Evidence’ hyperlink.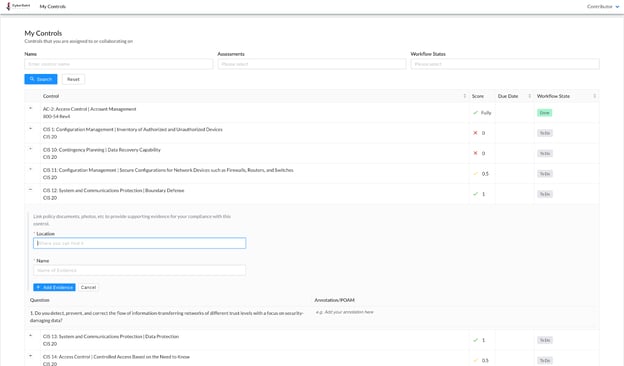
Contributors can also add annotations and POAMs by clicking into the ‘Annotation/POAM’ field.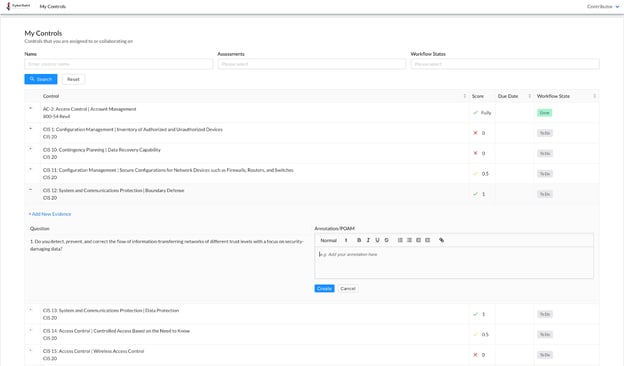
Reminder: You can further restrict Contributor access by hiding Current Score and Target Score by framework. To do so, follow the step-by-step guidance below:
- Navigate to the ‘Administration’ tab within the home navigation bar and select ‘Frameworks’ from the dropdown menu.
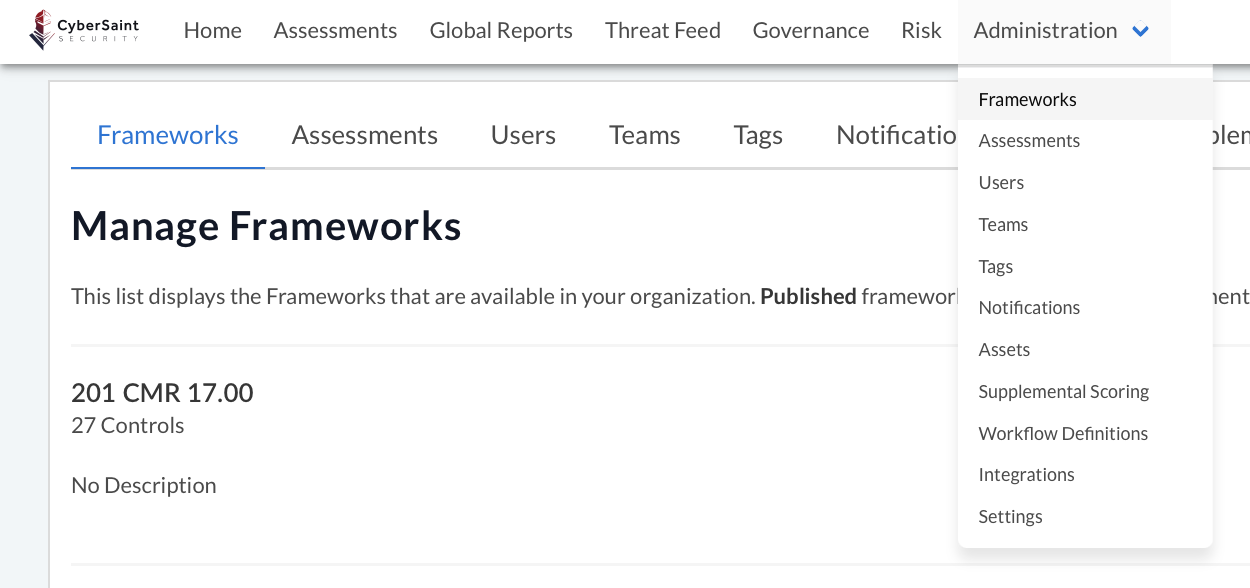
- Locate the framework you want to hide scores for and select ‘Manage Framework’ from the ‘Actions’ dropdown menu.
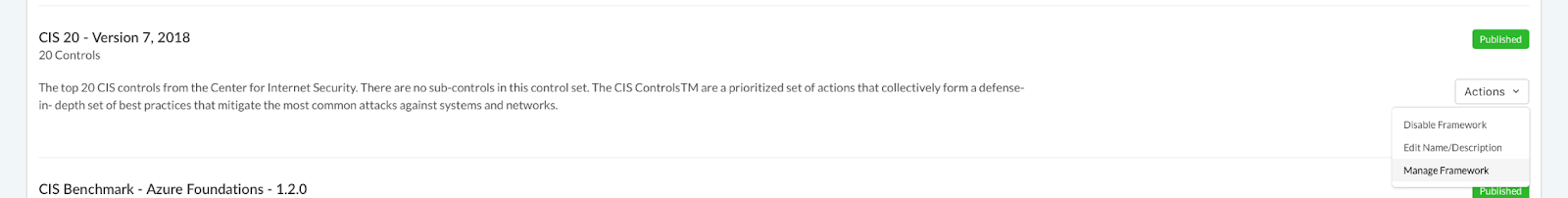
- From the ‘Manage Framework’ page, navigate to the ‘Field Configuration’ tab to the right of the ‘Metadata’ tab.
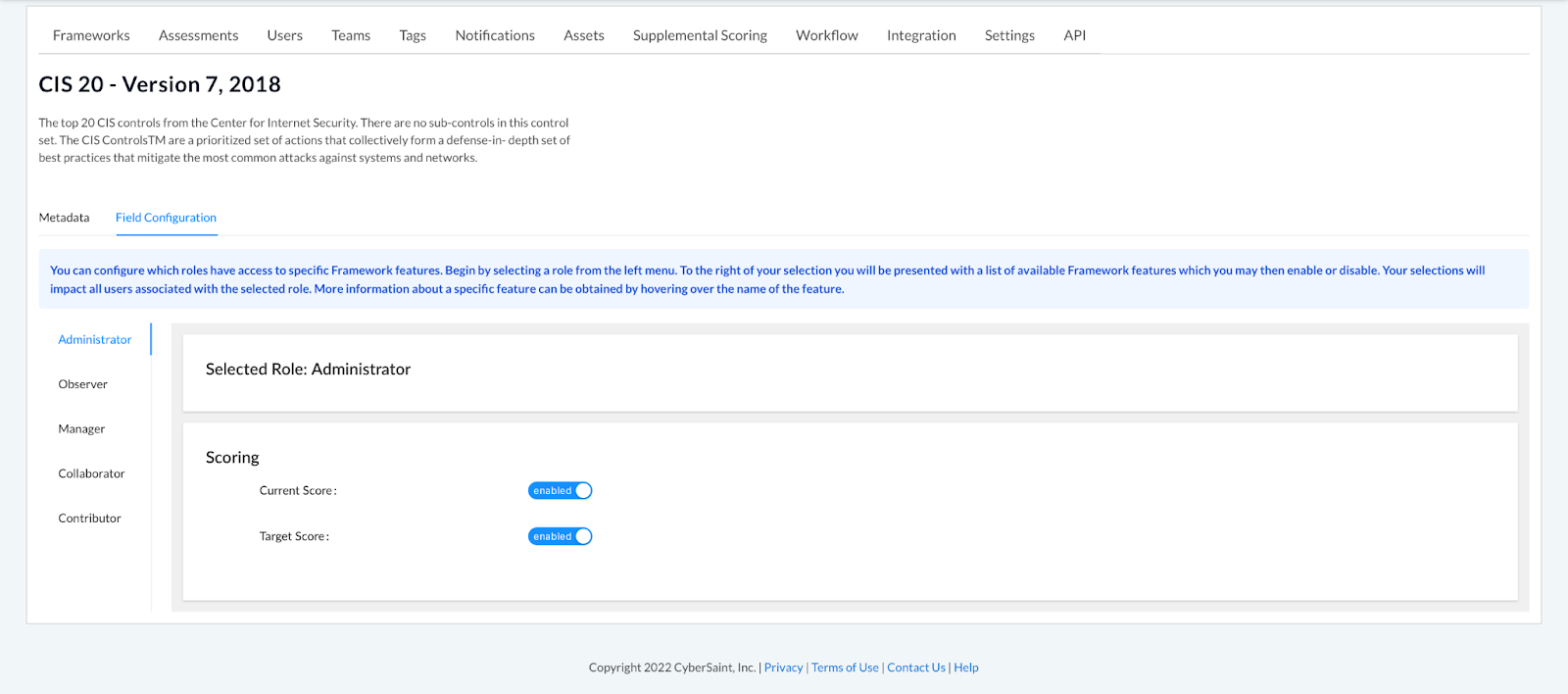
- Select the Contributor role from the menu on the left-hand side of the page.
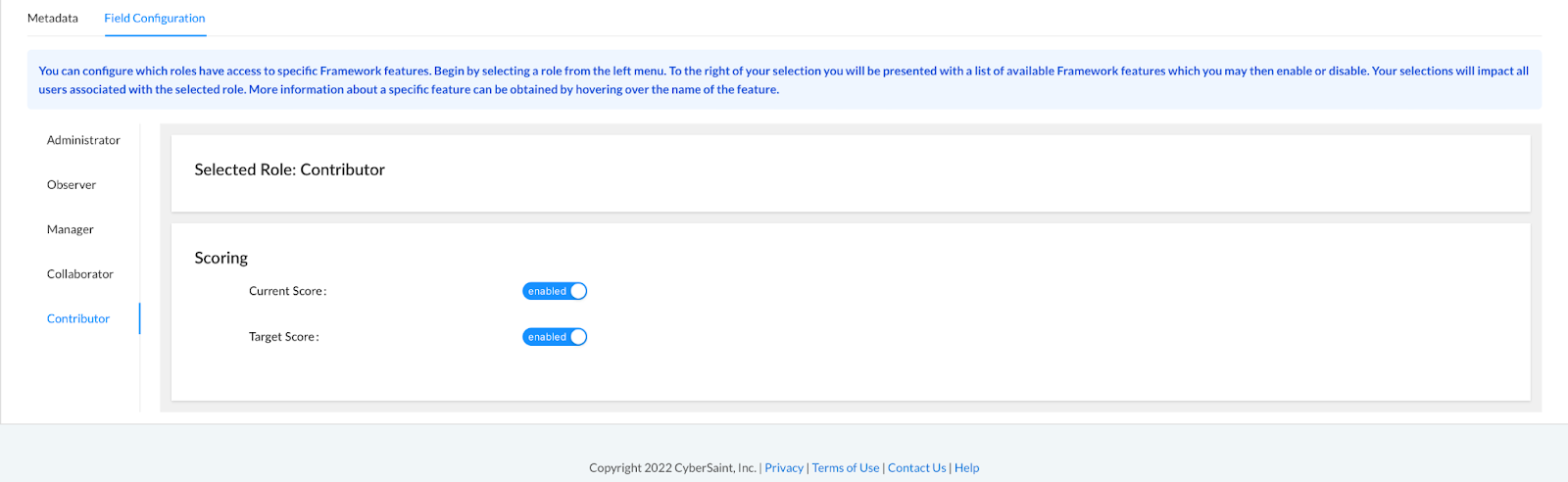
- Hide the current score or target score by using the corresponding blue toggle options.
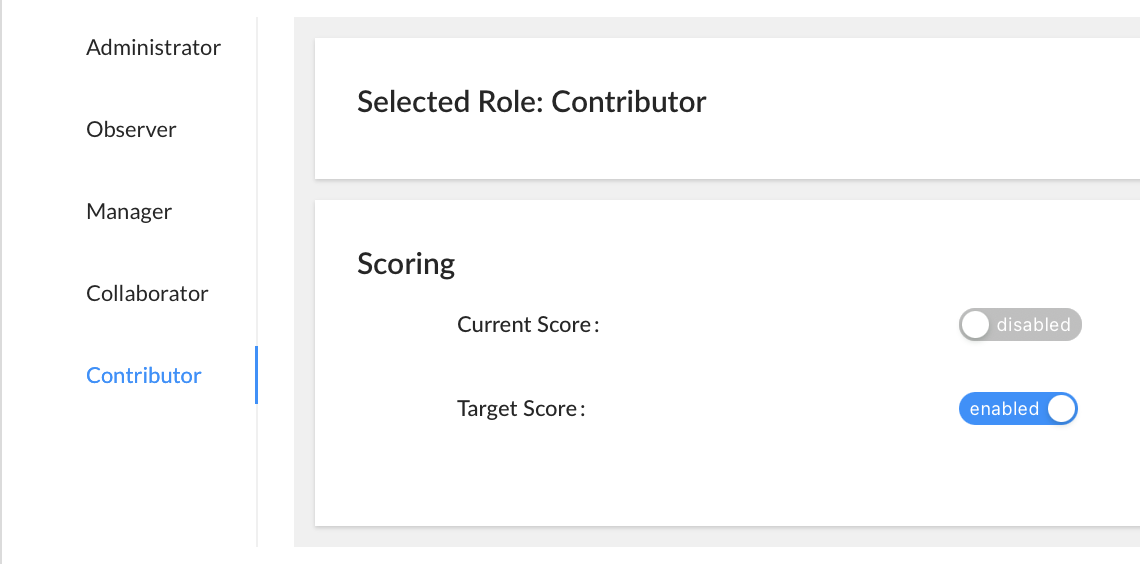
Note: If the Contributor is assigned controls from multiple frameworks where Current Score is hidden only for a subset of those frameworks, the ‘Score’ column will appear in the ‘My Controls’ tab; however, ‘Score’ cells corresponding to controls whose Current Score has been hidden will appear blank.
For additional information related to restricting Contributor access, please reach out to your dedicated Customer Success Manager.





.png)
.png)
.png)
%201.png)
.png)




