In today's hyper-connected world, where data is the lifeblood of businesses and individuals alike, the threat of cyberattacks looms large. From sophisticated malware infiltrations to targeted phishing schemes, the landscape of cyber threats constantly evolves, demanding proactive measures to manage cyber risks. This is where cyber risk analysis emerges as a crucial step of cyber risk management.
So, what exactly is cyber risk analysis? Imagine it as a comprehensive assessment that identifies, analyzes, and prioritizes potential cyber risks your organization might face.
Cyber risk analysis is a process that empowers you to work proactively in cyber risk management. By understanding your cyber risks, you can make informed decisions to mitigate them before they become costly data breaches or disruptive system failures.
As an organization's CISO or security leader, it’s invaluable to understand the company’s security posture and effectively analyze it to identify and prioritize measures according to severity and impact. CyberStrong's Cyber Risk Analysis empowers CISOs to benchmark their organization against industry peers.
Conduct Cyber Risk Analysis with the CyberStrong Solution
CyberSaint is now offering a free opportunity for organizations to leverage its advanced risk analysis capabilities. In this opportunity, you can discover your organization’s top 5 industry risks and related NIST 800-53 controls in just three clicks.
Step 1. Set up your Free Cyber Risk Analysis
After entering the relevant information, you will receive an email with access to CyberStrong.
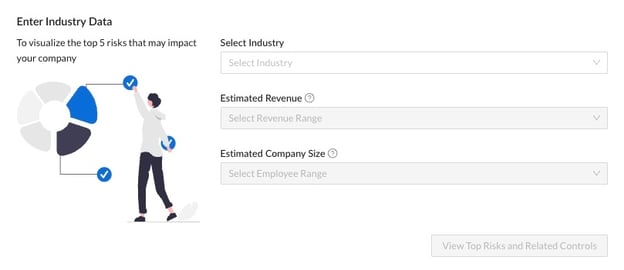
2. Enter Industry Data
Once in CyberStrong, you must enter three data points to help visualize your top 5 risks: Industry, Estimated Revenue, and Estimated Company Size. CyberSaint’s Risk Analysis model leverages a comprehensive historical cyber loss dataset to calculate your top 5 industry risks and related controls.
3. Review your Top Industry Cyber Risks
Once you've unlocked your top 5 cyber risks and related controls, we'll guide you through a data-driven approach to cyber risk management, from financializing cyber risks to prioritizing related controls and security investments. The annualized loss exposure (ALE) for each identified risk is based on the NIST 800-30 risk model but also supports the FAIR methodology.
Risk Data can empower CISOs to advocate for cyber investment and allocate resources effectively. Additionally, CISOs and business-side leaders can leverage risk data to report transparently and accurately on the organization’s risk posture to Board leaders.
CyberStrong, at its core, is a solution-driven platform that identifies, prioritizes, and guides efficient mitigation of cyber risks. An effective tool for analysts, risk and compliance managers, CISOs, and Boards, CyberStrong also offers automated and data-backed tools for executive reporting, assessments, governance, risk, and remediation.
Get your Free Cyber Risk Analysis here.





.png)
.png)
.png)
%201.png)
.png)